Authentication and Identities
Authentication is the process of identifying someone. This post attempts to shed some light on the process.
In a recent post, we saw a brief overview of authorization and authentication. This post attempts to shed some light on the process.
Principal and Identities
The relevant definition for principal is a person for whom another acts as an agent or representative.[1]
Your identity in a system represents you [the principal] in that system.
I am @gldraphael on Twitter. So, I am the principal and @gldraphael is my Twitter identity i.e. @gldraphael represents me on Twitter. If someone manages to tweet something using my phone (that's logged in as @gldraphael), people will assume it was I who tweeted it, because @gldraphael is my identity.
On a side note, some systems allow a principal to have multiple identities while others don't. For eg, it's completely okay for me to have two Twitter accounts. But I'm not allowed to have two Facebook accounts.[2]
A basic authentication system
The simplest authentication system would be a basic login screen that asks for a username and a password.
The username is your identity for the system (which could be a website, an app, etc.), and the password is the proof that the identity is yours.
Let's consider Jane [the principal] creating an email account. She creates an email account [email protected] [the identity] using mycathatesme:( as her password [proof]. Now to be able to send or view an email she'll first have to login using her email address and her password. Basically it's Jane telling the system: "I'm [principal] Jane [identity] and here's the proof. Let me in."
That's how we get through authentication in any system: provide it with your identity and the proofs that the identity is yours.
Authentication Factors
The most commonly used proof in auth systems is a password. Because only the owner of the identity (i.e. the real user aka principal) would ideally know the password he set for his identity for a given system. However, many other proofs could be used too. These proofs can be categorized into three different factors:
- Knowledge factor or what you know (eg. your password, personal information, etc.)
- Possession factor or what you have (eg. your device, an SMS sent to you, a link emailed to you, your smart card, your credit card's CVV, etc.)
- Inherence factors or what you are (physical features like fingerprints, voice, etc.) & what you do (behavioural patterns like search history, location patterns, phone usage patterns, keystroke dynamics, etc.)
Every factor is vulnerable to a set of attacks. For eg. I could steal what you know by recording everything you type on your device. By requiring proofs of different factors, the attack surface area is minimized.
That is, higher the number of authentication factors the system employs, higher the probability that the user-trying-to-authenticate is who he claims to be. Multiple authentication factors can improve the accuracy of the authentication system which means lesser chances of your identity getting compromised.
Google, for example, employs almost all of it: They require me to use my email address (identity) and password (what I know) to login. Followed by the 2FA step for which I'll need my phone (what I have). I can unlock an android phone using my fingerprint or face recognition (what I am). And whenever I login from an unusual place or a new computer (what I do) I get an email ensuring if it was really I that just logged in.
Revocability of Proofs
Not all proofs are the same. One important property of identity proofs is its degree of revocability. Higher the degree of revocability, the easier it gets to secure your identity after it's compromised.
I can change my password easily (in most systems) which makes it a proof with a high degree of revocability. But I cannot change my fingerprint which makes it a proof with a low (actually zero IMO) degree of revocability. If Mallory manages to steal my password, his efforts will be down the drain the moment I revoke my old password by changing it.[3] But if my fingerprint is stolen, it's stolen. It's not something I can revoke.
In most cases, inherence factors (what you are & what you do) have a really really low degree of revocability. This makes them weak and are only fit as a last line of defence. This is why fingerprints are only added in addition to another proof of a different factor (like a PIN or a password).
Identity Theft
Identity theft: The illegal use of someone else's personal information (such as a Social Security number) especially in order to obtain money or credit.[4]
In real life, an identity of a person is attached to the person [principal]. This is not possible in software systems, because they can't (at the moment) interact with humans the way we do. And so the person and his identities are separate entities. The only thing that gives the person [principal] exclusive access to his identities are his proofs.
Now here's the thing: Your proofs can be stolen. If that happens you're not the only one who has access to your identity anymore. Which means your identity is stolen too right? Kind of.
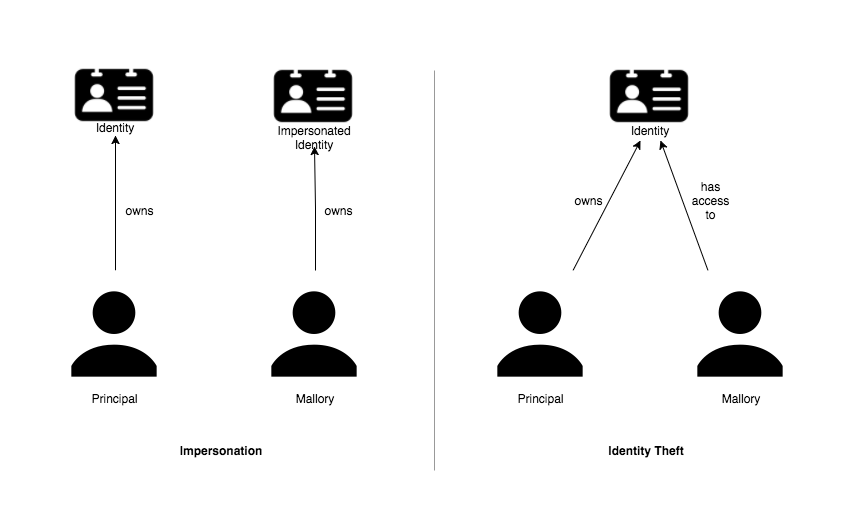
Identity theft vs Impersonation
In identity theft, the attacker manages to gain [partial or complete] access to your identity by stealing your proofs. Impersonation on the other hand is where the attacker creates a new identity that resembles yours.
Summary
You are not your identity. But your identity represents you. To keep it safe, you got to keep your proofs safe.
Principal definition taken from the Oxford American College Dictionary. Source (See Noun 3) ↩︎
From the Facebook Help Centre and the Facebook Community Standards. ↩︎
Changing the password is a good start but might not be sufficient to keep Mallory out. For instance if he got to know your password using a keylogger, you would need to get rid of it as well. ↩︎
Identity theft definition taken from the Merriam-Webster Dictionary. Source. ↩︎